Oh, what a tangled web we weave when first we practice to deceive! A major supply chain attack has shaken the crypto world to its core, putting users everywhere on high alert. Ledger’s CTO, Charles Guillemet, is waving the red flag, urging everyone to take cover and maybe even invest in a hardware wallet. 🛡️
- Ledger’s CTO, Charles Guillemet, warns of a sneaky JavaScript supply chain attack that’s quietly swapping out crypto wallet addresses. 😱
- A whopping 18 popular NPM packages have been compromised, including the ever-trusty ‘chalk’ and ‘debug,’ which got a little too much of a makeover after a developer’s account was hijacked. 😬
- So far, only $497 has been stolen, but with over 2 billion downloads, it’s like the attacker has a golden ticket to a crypto candy store. 🍭
- Big names like Uniswap, Jupiter, and MetaMask are reassuring us that our precious funds are still safe, but you can never be too careful. 🔒
It all started with a hacked Node Package Manager (NPM) account, and now billions of downloads later, the security of countless dApps and crypto transactions is hanging by a thread. 🧵
“The NPM account of a reputable developer has been compromised. The affected packages have already been downloaded over 1 billion times,” Guillemet warned, sounding like a digital Paul Revere. 🚨
🚨 There’s a large-scale supply chain attack in progress: the NPM account of a reputable developer has been compromised. The affected packages have already been downloaded over 1 billion times, meaning the entire JavaScript ecosystem may be at risk.
The malicious payload works…
– Charles Guillemet (@P3b7_) September 8, 2025
Guillemet went on to explain that the malware acts as a crypto clipper, silently hijacking wallet addresses during transactions and rerouting funds to the attacker’s wallets. It’s like a digital pickpocket, but with a lot more zeros. 💸
“If you use a hardware wallet, pay attention to every transaction before signing and you’re safe. If you don’t, refrain from making any on-chain transactions for now,” he advised, adding a bit of practical wisdom to the chaos. 📝
NPM hack: How the breach happened
Turns out, 18 popular NPM packages were found to be compromised, including the likes of ‘chalk,’ ‘debug,’ and ‘strip-ansi.’ The attack, which took place on Sept 8, is one of the largest in recent memory, affecting libraries with a staggering 2 billion weekly downloads. 🌐
The attack reportedly began with a phishing email masquerading as official NPM support. The victim was none other than Qix-, a well-respected developer whose NPM account was hijacked, allowing the attackers to inject malicious updates into beloved JavaScript libraries. 🕵️♂️
Once installed, the malware silently swaps out copied crypto addresses with lookalike ones controlled by the hacker, thanks to some clever Levenshtein distance logic. It’s like a digital game of “spot the difference,” but with your hard-earned crypto on the line. 🎮
Researchers have identified one main wallet address linked to the attack, though they suspect there are others involved. Despite the relatively small amount of $497.96 stolen so far, the potential impact is massive given the popularity of the affected packages. 🤔
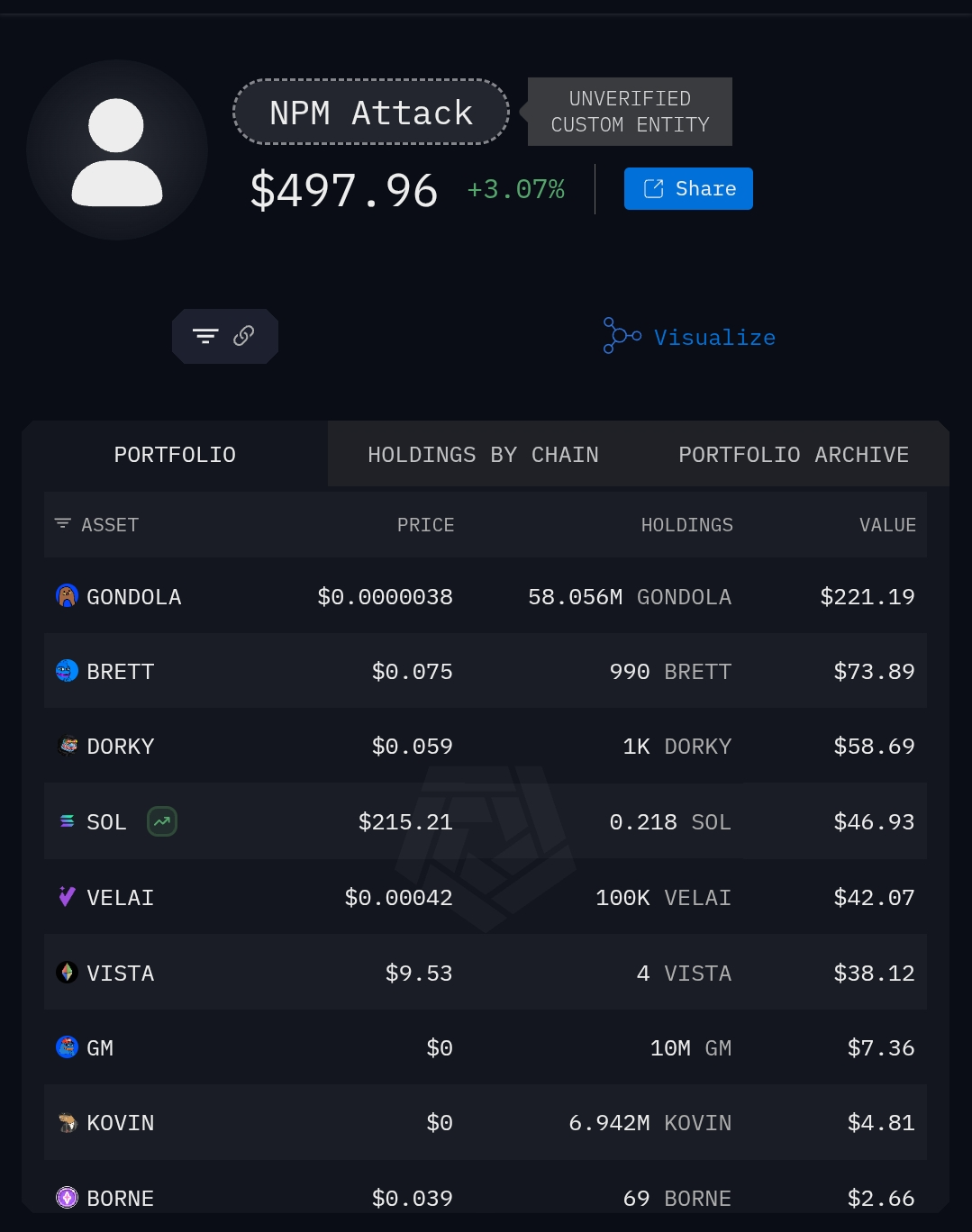
While the immediate financial impact might seem negligible, the sheer scale of the affected packages means the potential for disaster is enormous. 🌋
Community response and prevention
Several projects and protocols, including Uniswap, SUI, and Jupiter, have come forward to say they’re not affected but are advising caution. Cryptocurrency wallets like Ledger and MetaMask are touting their multi-layered security measures, just in case. 🛡️
But wait, there’s more! On the same fateful day, Swiss crypto wealth platform SwissBorg reported a $41 million exploit via a partner API, affecting 1% of users. And if that wasn’t enough, the Ethereum L2 project Kinto announced its shutdown after a July exploit drained 577 ETH, leaving the team high and dry. 🙁
These attacks serve as a stark reminder of the growing sophistication of crypto threats. Moving forward, users, developers, and platforms need to step up their game with more secure practices and thorough package audits. It’s time to put on your digital armor and get ready for battle. ⚔️
Read More
- Clash Royale Best Boss Bandit Champion decks
- Mobile Legends January 2026 Leaks: Upcoming new skins, heroes, events and more
- Clash Royale Furnace Evolution best decks guide
- Vampire’s Fall 2 redeem codes and how to use them (June 2025)
- Best Hero Card Decks in Clash Royale
- Mobile Legends: Bang Bang (MLBB) Sora Guide: Best Build, Emblem and Gameplay Tips
- Best Arena 9 Decks in Clast Royale
- Clash Royale Witch Evolution best decks guide
- Brawl Stars Steampunk Brawl Pass brings Steampunk Stu and Steampunk Gale skins, along with chromas
- Brawl Stars December 2025 Brawl Talk: Two New Brawlers, Buffie, Vault, New Skins, Game Modes, and more
2025-09-09 12:32