Author: Denis Avetisyan
As robotics technology becomes increasingly accessible, the potential for misuse raises critical questions about safeguarding international peace and stability.
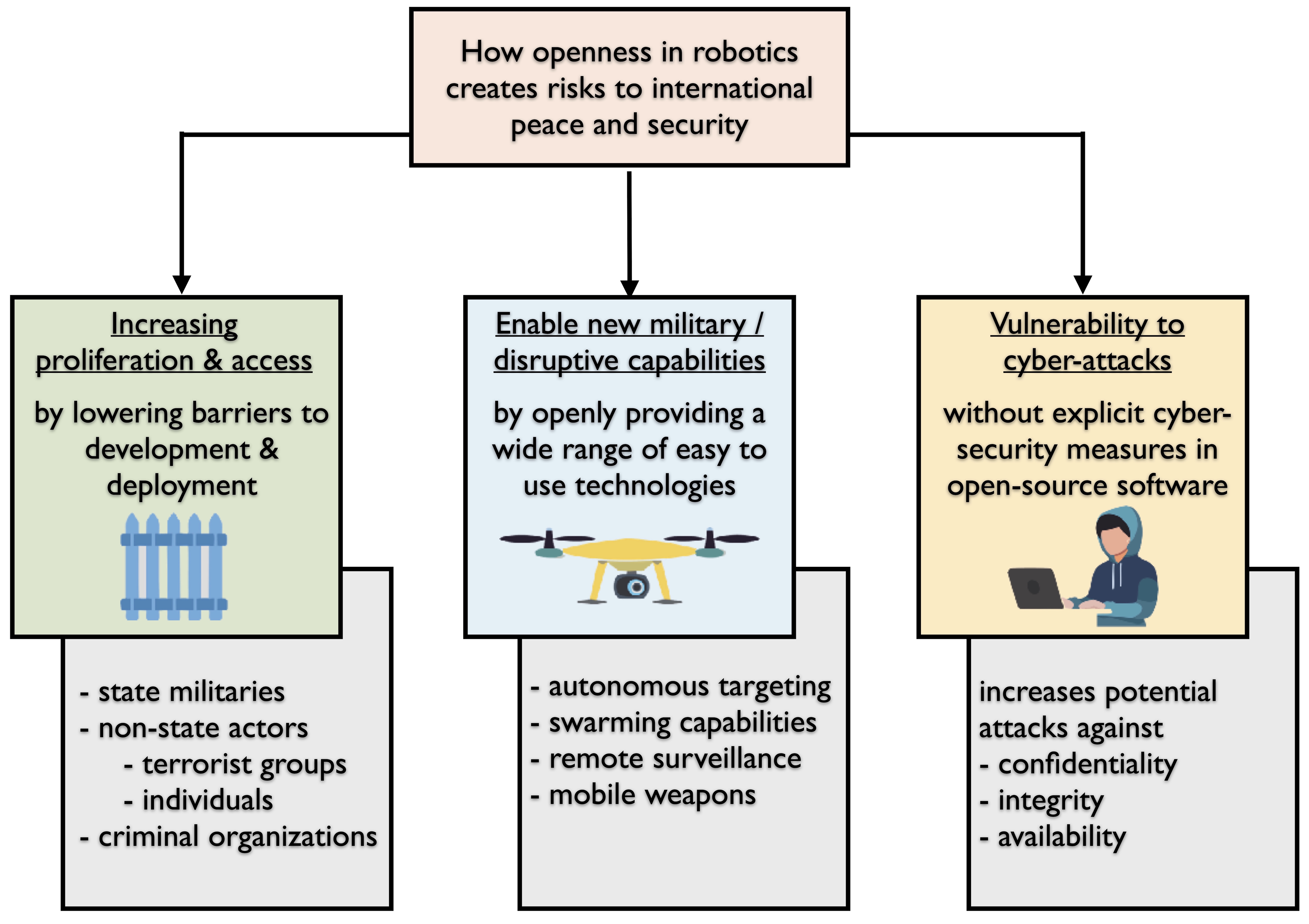
This review assesses the dual-use risks inherent in open robotics innovation and proposes strategies for responsible development and risk mitigation.
While open innovation is widely lauded for accelerating progress in robotics, its inherent accessibility simultaneously exacerbates dual-use risks with potentially significant implications for international security. This paper, ‘Is open robotics innovation a threat to international peace and security?’, examines how the lowered barriers to entry in robotics development-unlike those present in fields like AI or weapons of mass destruction-create novel challenges for responsible innovation and risk mitigation. We argue that proactive strategies-encompassing education, incentivized risk assessment, moderated diffusion of sensitive materials, and clearly defined red lines-are crucial for navigating this complex landscape. Can the robotics community forge a path toward responsible self-regulation before these risks fully materialize, or will external oversight become necessary?
The Expanding Frontier: Robotics, Vulnerabilities, and Emerging Risks
The expanding integration of robotics into daily life promises substantial societal advantages, ranging from enhanced manufacturing and healthcare to improved disaster response and agricultural efficiency. However, this very sophistication introduces a complex array of security vulnerabilities and dual-use risks previously unseen in conventional technologies. As robotic systems become more autonomous and interconnected, they present attractive targets for malicious actors seeking to disrupt critical infrastructure, steal sensitive data, or even inflict physical harm. Furthermore, the same capabilities that enable beneficial applications – such as precise manipulation, navigation, and data analysis – can be readily repurposed for harmful ends, creating a significant challenge for policymakers and security professionals striving to anticipate and mitigate these emerging threats. This duality demands a proactive approach to robotic security, encompassing robust design principles, stringent testing protocols, and ongoing vigilance against evolving cyber and physical attacks.
The conflict in Ukraine provided a sobering demonstration of the speed with which commercially available robotics can be adapted for military purposes. Initially designed for civilian applications – such as agricultural surveying or package delivery – drones were swiftly repurposed for reconnaissance, artillery spotting, and even direct attacks. This rapid transition exposed a significant deficiency in anticipating and mitigating the security implications of dual-use technologies. Existing risk management strategies, largely focused on bespoke military systems, proved inadequate in addressing the challenge posed by easily obtainable, mass-produced robotic platforms. The conflict underscored the need for proactive measures, including enhanced monitoring of component supply chains, development of countermeasures against drone swarms, and international cooperation to establish responsible robotics usage guidelines, before similar technologies are exploited in future conflicts or by non-state actors.
The foundation of much modern robotics relies heavily on open-source software, a collaborative approach that dramatically accelerates innovation and reduces development costs. However, this very openness introduces significant security vulnerabilities, as demonstrated by the recent compromise of XZ Utils, a widely used data compression library. Attackers successfully inserted malicious code into the library’s codebase, potentially granting them access to a vast number of systems, including those controlling robotic platforms. This incident underscores a critical risk within the robotics ecosystem: while open-source fosters progress, the lack of centralized control and rigorous vetting processes can create avenues for exploitation, allowing malicious actors to introduce backdoors or manipulate functionality with far-reaching consequences. The XZ Utils case serves as a stark warning that even seemingly benign components can become critical points of failure, demanding a paradigm shift towards more robust security practices throughout the entire open-source supply chain.
The increasing accessibility of both hardware and software is dramatically reshaping the landscape of robotic threats. Once requiring significant financial investment and specialized expertise, the capacity to build and deploy sophisticated robotic systems – or to maliciously manipulate them – is now within reach of a far wider range of actors. The plummeting cost of components like microcontrollers, sensors, and actuators, coupled with the widespread availability of open-source robotics software frameworks and pre-trained algorithms, has effectively lowered the barrier to entry. This democratization, while fostering innovation, concurrently presents heightened risks, as malicious actors can readily acquire the necessary tools to repurpose robots for harmful activities, develop autonomous weapons, or launch coordinated cyberattacks targeting critical infrastructure – all with comparatively limited resources and technical skill.
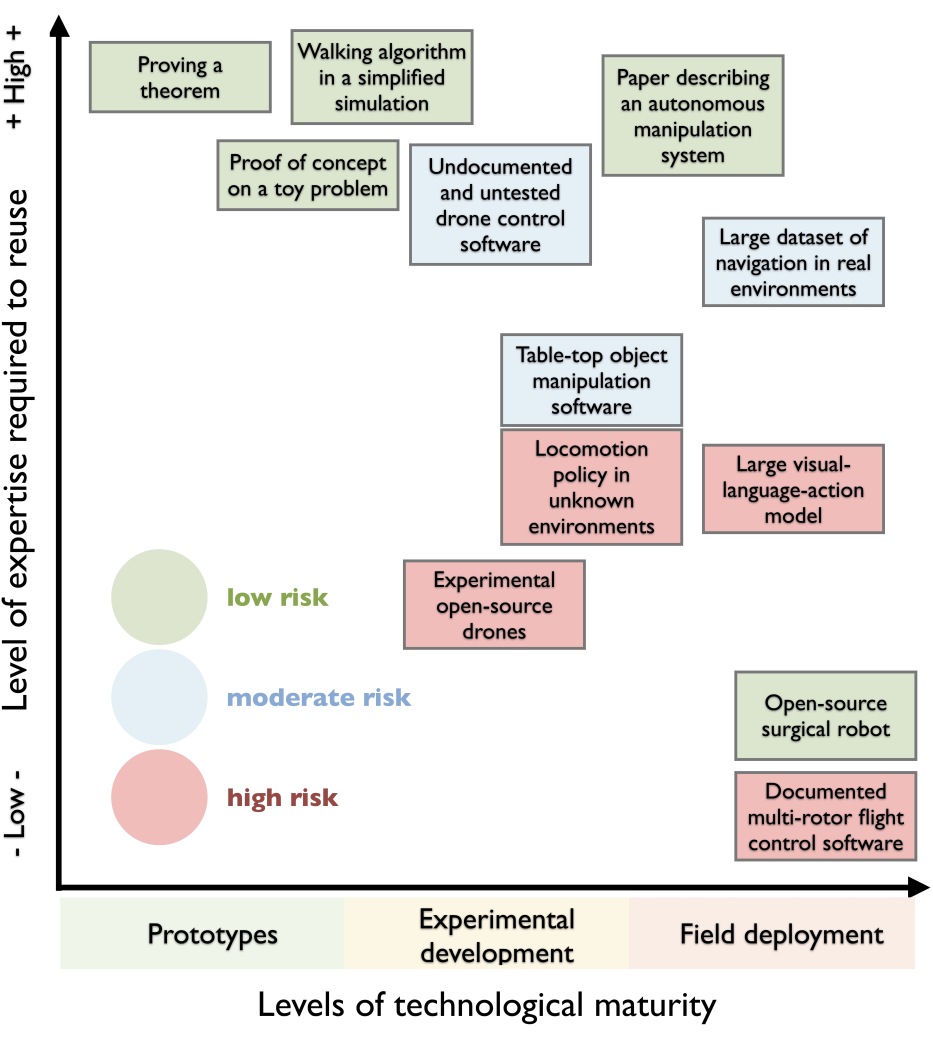
The Expanding Attack Surface: Enabling Technologies and System Accessibility
The increasing accessibility of robotic system development is directly correlated to advancements in 3D printing and the proliferation of open-source software frameworks. 3D printing allows for rapid prototyping and customization of robotic hardware, reducing both cost and time to deployment. Simultaneously, Robotic Operating System (ROS) and Betaflight provide pre-built libraries, tools, and algorithms, significantly lowering the barrier to entry for developers. This combination enables both legitimate innovation and malicious modification; individuals and organizations can readily create, adapt, and deploy robotic systems without requiring extensive specialized expertise, thereby expanding the potential attack surface to include a wider range of actors and a greater number of vulnerable systems. The open-source nature of these tools also facilitates the identification and exploitation of vulnerabilities, as code is publicly available for review and modification.
The open-source ground control software QGroundSuite has been demonstrably exploited to modify drone firmware, enabling malicious actors to bypass geofencing restrictions and operational safeguards. Researchers have shown that compromised QGroundSuite installations can be used to upload altered flight parameters, effectively weaponizing commercially available drones. This vulnerability stems from the software’s permissive architecture and the lack of robust security checks during firmware updates. Notably, the ease with which QGroundSuite can be modified and redistributed, coupled with its widespread adoption in both hobbyist and professional drone operations, presents a significant risk, allowing non-state actors to leverage readily available tools for disruptive or harmful purposes without requiring specialized technical expertise.
The increasing dependence on large datasets for training robotic systems, coupled with the integration of generative AI models, presents novel attack vectors related to data integrity and model security. Data poisoning attacks involve the intentional introduction of malicious or misleading data into training sets, potentially causing robots to exhibit unpredictable or harmful behavior. Simultaneously, manipulation of generative AI models – through techniques like adversarial training or model backdoors – can allow adversaries to subtly alter a robot’s decision-making process or create exploitable vulnerabilities. These attacks differ from traditional software exploits by targeting the foundational data and algorithms that govern robotic behavior, making detection and mitigation significantly more complex and requiring robust data validation and model monitoring strategies.
The adoption of Llama models – large language models developed by Meta – by both the United States and Chinese militaries highlights the risks associated with dual-use technologies. These models, initially intended for commercial applications like chatbots and content generation, possess capabilities readily adaptable to military functions, including intelligence analysis, strategic planning, and potentially autonomous systems control. This parallel development and deployment by geopolitical competitors creates a dynamic where advancements in model capabilities are immediately mirrored, potentially leading to an escalation cycle driven by the need to maintain a technological advantage. The lack of international governance specifically addressing the military applications of such broadly available AI models further exacerbates the risk of unintended consequences and an accelerated arms race in artificial intelligence.
Toward Proactive Risk Management: Assessment and Mitigation Strategies
Proactive risk mitigation in robotics necessitates a systematic and comprehensive risk assessment process. This involves identifying potential hazards associated with robotic systems, analyzing the vulnerabilities that could be exploited, and evaluating the potential harms resulting from those exploits. Risk assessments should consider all phases of a robot’s lifecycle, from design and development through deployment, operation, and decommissioning. The scope of assessment must include not only technical failures – such as hardware malfunctions or software bugs – but also potential misuse, unintended consequences, and impacts on safety, security, privacy, and societal values. A thorough assessment forms the basis for developing targeted mitigation strategies, prioritizing resources, and establishing appropriate safeguards to minimize risk and ensure responsible innovation.
The IEEE Robotics and Automation Society (RAS) and EuRobotics are positioned to significantly influence responsible robotics development through several mechanisms. These include the formulation of technical standards – addressing interoperability, safety, and performance – and the dissemination of best practices via conferences, workshops, and publications. Both organizations actively fund and coordinate research initiatives focused on ethical considerations and societal impact. Furthermore, they provide platforms for multi-stakeholder dialogue involving researchers, industry representatives, policymakers, and the public, fostering a collaborative approach to risk mitigation and the establishment of norms for robotic systems. Their collective efforts aim to translate ethical principles into actionable guidelines and technical specifications, promoting accountability and minimizing potential harms associated with advanced robotics technologies.
The establishment of clearly defined “red lines” in robotics development is critical for mitigating potential harms, particularly concerning the creation of autonomous weapons systems (AWS). These lines delineate unacceptable functionalities or deployment scenarios, focusing on preventing systems capable of selecting and engaging targets without meaningful human control. Current international discussions regarding AWS emphasize the need for prohibiting systems that lack sufficient human oversight, acknowledging the risks of unintended escalation, accidental targeting of civilians, and the lowering of the threshold for armed conflict. Defining these boundaries requires international cooperation and the development of enforceable standards, going beyond self-regulation by individual organizations or nations to ensure responsible innovation and uphold ethical considerations related to human safety and international humanitarian law.
Currently, pre-publication servers for robotics research, such as ArXiv, lack systematic screening for potential biosecurity and safety risks. This contrasts with pre-print servers in the life sciences, BioRxiv and medRxiv, which employ editorial and peer-review processes to identify and address concerns related to dual-use research and biosafety. Implementing a similar pre-publication screening process for robotics papers could proactively identify research with potential for misuse – for example, in the development of autonomous systems with harmful applications – and facilitate mitigation strategies before widespread dissemination. This screening would not necessarily constitute peer review, but rather a focused assessment to flag potentially problematic research for further scrutiny or responsible disclosure.
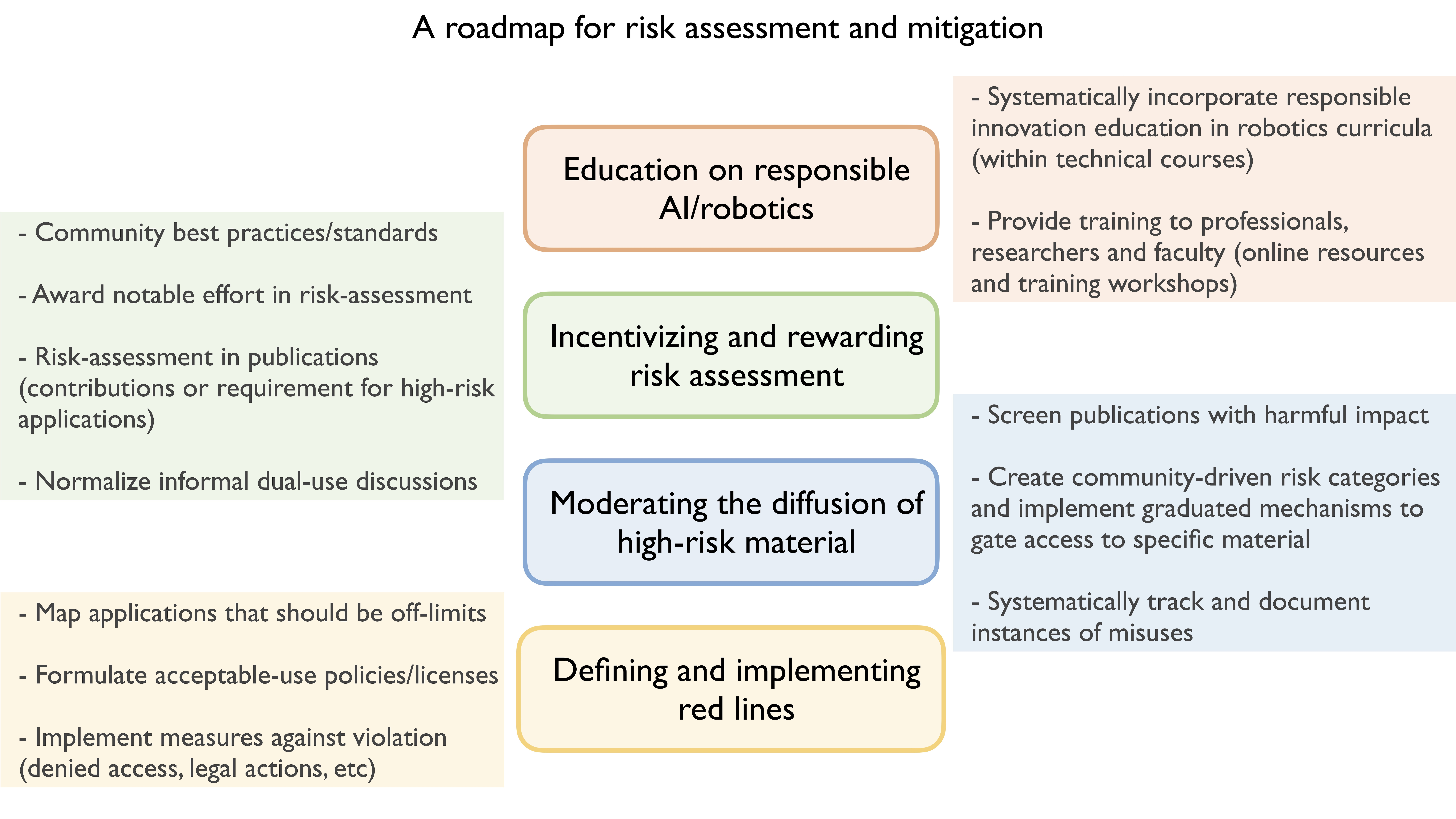
Charting a Course for Responsible Innovation and Collective Security
The advancement of robotics presents a significant dual-use dilemma, requiring a proactive shift towards responsible innovation. This entails deliberately integrating ethical considerations into the design, development, and deployment of robotic systems, ensuring that potential societal benefits consistently outweigh the risks. Rather than simply focusing on technological capabilities, this approach prioritizes alignment with human values, promoting applications that enhance well-being, sustainability, and equity. By embedding ethical frameworks within the innovation process, developers can anticipate and mitigate potential harms, fostering public trust and enabling the safe and beneficial integration of robotics into everyday life. Ultimately, responsible innovation is not a constraint on progress, but rather a vital pathway to unlocking the full potential of robotics while safeguarding collective security and promoting a more just and equitable future.
The increasing accessibility of open-source robotics tools, while fostering innovation, simultaneously presents escalating cybersecurity vulnerabilities. This broadened access lowers the barrier for malicious actors to adapt and deploy robotic systems for harmful purposes, demanding a proactive shift towards robust defense strategies. Current cybersecurity protocols, often designed for traditional software, prove inadequate when applied to the unique challenges posed by physical robotic systems and their complex interactions with the real world. Consequently, significant investment and focused research are crucial to develop novel security measures-including enhanced authentication protocols, intrusion detection systems tailored for robotics, and secure software update mechanisms-to mitigate potential threats and safeguard critical infrastructure from exploitation. This necessitates a continuous cycle of vulnerability assessment, threat modeling, and adaptive security implementations to stay ahead of evolving risks in the open-source robotics landscape.
The escalating advancement of robotics presents complex global security challenges that transcend national borders, necessitating a concerted international approach. Effective mitigation of risks associated with autonomous systems demands the open exchange of information regarding research, development, and potential malicious applications. Collaborative efforts can foster a shared understanding of emerging threats, allowing for the proactive development of countermeasures and standardized safety protocols. Such cooperation isn’t simply about intelligence sharing; it requires the establishment of international norms and agreements governing the responsible use of robotics, ensuring that innovation benefits humanity while minimizing the potential for destabilizing consequences. Without a unified, globally-coordinated strategy, the security implications of rapidly evolving robotic technologies risk becoming fragmented and ultimately, less manageable.
A proactive approach to mitigating the dual-use risks inherent in open robotics research is detailed within this work, outlining four key avenues for action. Firstly, enhanced education aims to foster a deeper understanding of potential misuse among researchers and developers. Simultaneously, incentivization strategies encourage the creation of safety-focused designs and responsible innovation practices. Complementing these are moderation efforts, designed to facilitate community oversight and address potentially harmful developments before they escalate. Crucially, the roadmap also emphasizes the need for clearly defined red lines – specific technological boundaries and applications that represent unacceptable risks – providing a framework for preemptive action and safeguarding against malicious exploitation of increasingly accessible robotic technologies.
“`html
The pursuit of open robotics innovation, as detailed in the analysis, introduces a complex interplay of benefits and risks. The study rightly points to the emergence of dual-use technologies as a primary concern, demanding careful consideration. This resonates deeply with John von Neumann’s observation: “If you say you’re going to play a game, you must accept the rules.” The open nature of the field, while fostering rapid development, necessitates a proactive acceptance of the inherent security implications and a corresponding commitment to responsible innovation. Ignoring these rules, optimizing for speed without considering systemic vulnerabilities, creates a fragile system where dependencies become the true cost of freedom. The architecture of security, like any good system, remains invisible until it breaks.
The Road Ahead
The accelerating democratization of robotics, while intuitively positive, reveals a fundamental tension. Each optimization-increased accessibility, enhanced performance, broadened application-introduces a corresponding point of potential instability. The architecture is the system’s behavior over time, not a diagram on paper, and that behavior is increasingly shaped by actors beyond traditional centers of control. To focus solely on technical solutions to dual-use risks is to treat symptoms, not the underlying condition: a distributed system with emergent properties that defy simple containment.
Future work must move beyond static risk assessments. A truly robust approach requires dynamic modeling of the robotics innovation ecosystem itself, accounting for the interplay between open-source development, commercial interests, and the evolving threat landscape. The challenge isn’t preventing innovation-an impossible and undesirable goal-but rather fostering a culture of anticipatory governance within the robotics community.
Ultimately, the question isn’t whether open robotics poses a threat, but whether the community can develop the self-awareness and collective mechanisms to manage the inherent tensions it creates. The system will find its equilibrium; the critical task is to influence the forces shaping that outcome, acknowledging that even the most carefully designed interventions will inevitably introduce new, unforeseen consequences.
Original article: https://arxiv.org/pdf/2601.10877.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Clash Royale Best Boss Bandit Champion decks
- Vampire’s Fall 2 redeem codes and how to use them (June 2025)
- World Eternal Online promo codes and how to use them (September 2025)
- Best Arena 9 Decks in Clast Royale
- Country star who vanished from the spotlight 25 years ago resurfaces with viral Jessie James Decker duet
- ‘SNL’ host Finn Wolfhard has a ‘Stranger Things’ reunion and spoofs ‘Heated Rivalry’
- M7 Pass Event Guide: All you need to know
- Mobile Legends January 2026 Leaks: Upcoming new skins, heroes, events and more
- Kingdoms of Desire turns the Three Kingdoms era into an idle RPG power fantasy, now globally available
- Solo Leveling Season 3 release date and details: “It may continue or it may not. Personally, I really hope that it does.”
2026-01-19 09:26